Website security has evolved from reactive defense to proactive, AI-enhanced protection integrated from the ground up.
The state of web cybersecurity in 2025
Cybersecurity has never been more critical. The numbers for 2025 reveal a concerning reality: cybercrime is projected to cost $10.5 trillion globally, with some estimates reaching as high as $23 trillion by 2027. Organizations now face an average of 1,925 cyber attacks per week, representing a 47% increase from 2024.
Artificial intelligence is transforming the threat landscape. Cybercriminals now leverage AI to automate attacks, create convincing deepfakes, and personalize phishing campaigns. Supply chain attacks are exploding, with 45% of global enterprises expected to experience this type of attack by the end of 2025.
Small and medium businesses remain particularly vulnerable, representing 75% of attack targets. This vulnerability stems from limited security budgets and insufficient awareness of cyber risks. The education sector leads targeted attacks with 4,484 weekly attacks per organization, followed by government and telecommunications.
A few more figures:
- 978 million people affected by cyberattacks each year
- 1 in 2 French companies targeted by a cyberattack in 2024
- Cybercrime costs $6 trillion annually
- 30% data theft
- 29% denial of service
- 24% data encrypted by ransomware
- 23% identity theft
DDoS Protection: Your first line of defense
Understanding modern DDoS Attacks
Distributed Denial of Service (DDoS) attacks have evolved dramatically. In Q1 2025 alone, Cloudflare blocked 20.5 million attacks - nearly matching the entire 2024 total of 21.3 million. Attack sizes have reached unprecedented levels, with the average DDoS attack increasing by 69% year-over-year.
Modern attackers leverage AI and machine learning to optimize attack patterns and evade traditional detection systems. Hyper-volumetric attacks exceeding 1 Tbps are now common, with Cloudflare reporting approximately 8 attacks per day at this scale during Q1 2025.
Essential protection solutions
Modern anti-DDoS solutions operate across multiple layers:
- Network Layer Protection (L3-L4): Traffic filtering at IP and transport levels, capable of absorbing massive volumetric attacks. Leading providers like Cloudflare offer 388 Tbps capacity across 330+ cities globally.
- Application Layer Defense (L7): Behavioral analysis of HTTP/HTTPS traffic to identify malicious requests. This layer uses machine learning to distinguish legitimate traffic from sophisticated application-layer attacks.
- Proactive Mitigation: Modern systems employ predictive algorithms to detect attack precursors and automatically activate countermeasures. Sub-second mitigation is now standard, with some solutions achieving zero-second response times.
- Hybrid Protection: The most effective approach combines cloud-based scrubbing with on-premises appliances, providing both scalability and low-latency local protection.
TLS/SSL Certificates: securing communications
Evolution to TLS 1.3
The TLS 1.3 protocol establishes itself as the new standard in 2025. It offers crucial improvements over previous versions: enhanced encryption algorithms, faster connections, and elimination of obsolete cryptographic methods.
Modern SSL/TLS certificates integrate Perfect Forward Secrecy, protecting past communications even if a private key is compromised. The protocol reduces handshake complexity, improving both security and performance.
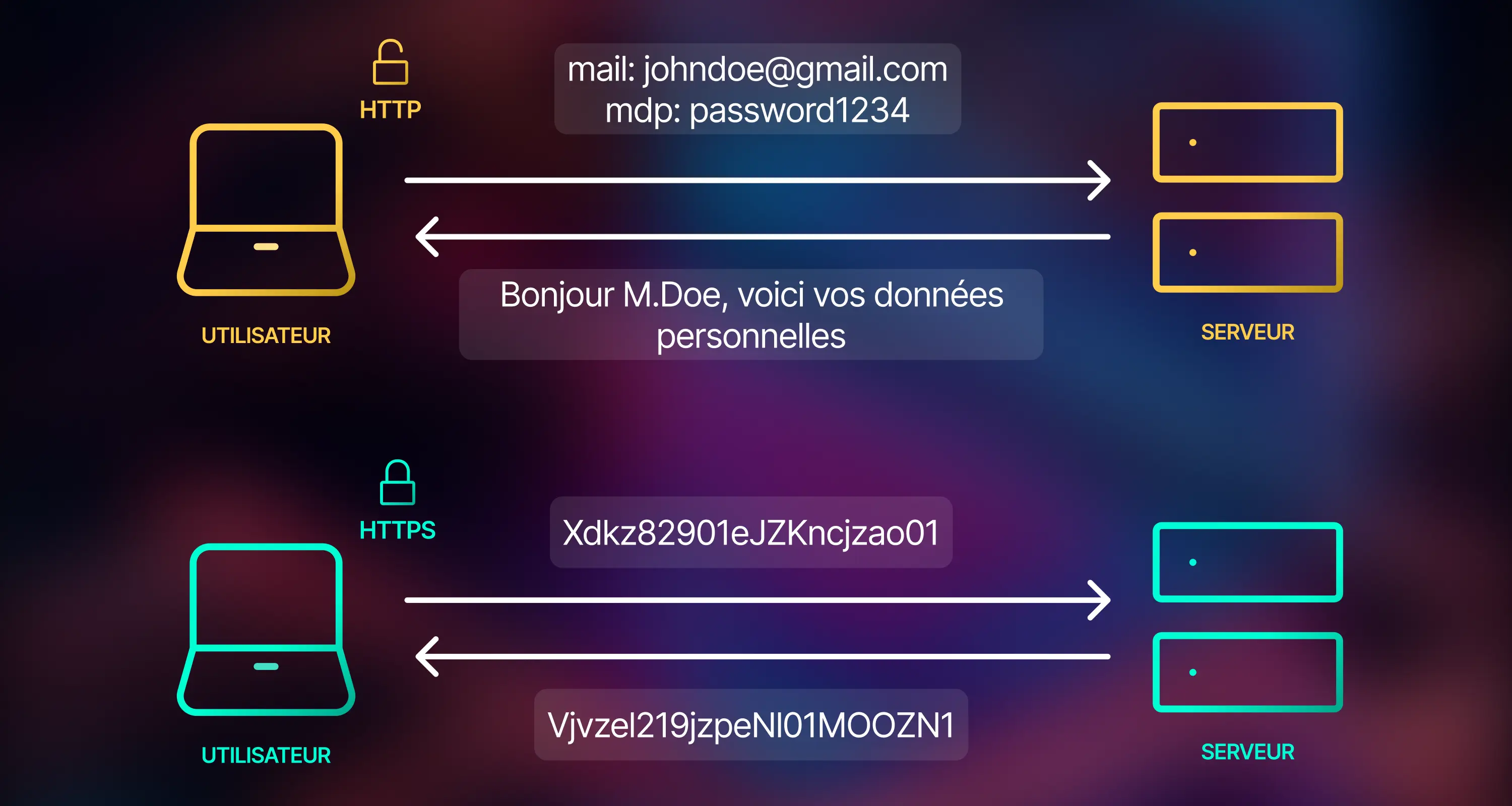
Certificate types for different needs
- Domain Validated (DV) Certificates: Automated validation for informational sites and blogs, with free options available from providers like Let's Encrypt.
- Organization Validated (OV) Certificates: Comprehensive identity verification recommended for business websites and corporate applications.
- Extended Validation (EV) Certificates: Highest validation level essential for e-commerce and financial sites, though browser indicators are evolving.
Learn more about web security: SSL, TLS, and HTTPS
Automation and management
Certificate authorities like Let's Encrypt provide free certificates with automated renewal via the ACME protocol. This approach eliminates human error and ensures continuous security. Modern platforms like Webflow automatically provision and renew SSL certificates, providing seamless security.
HTTP/3 and QUIC: The web security revolution
A paradigm shift
HTTP/3, based on Google's QUIC protocol, represents a fundamental change in web security. Unlike HTTP/2, which adds encryption on top of TCP, HTTP/3 natively integrates TLS 1.3 encryption into the transport layer.
Unique security advantages
Mandatory Encryption: All HTTP/3 connections are encrypted by default, eliminating the risk of unencrypted communications.
Enhanced Network Attack Resistance: QUIC's integrated security architecture provides better protection against man-in-the-middle attacks.
Performance and Security: Secure connection establishment in a single round-trip (0-RTT) for established connections, with built-in replay attack protection.
Adoption and support
Facebook streams 75% of content via HTTP/3, and approximately 30% of European web traffic uses this protocol. Major browsers natively support HTTP/3, facilitating widespread adoption. Early data shows improved resilience against DDoS attacks due to QUIC's integrated congestion control.
Authentication and access control
Multi-Factor Authentication (MFA)
Multi-factor authentication becomes indispensable as cybercrime losses to authorities increased 22% between 2022 and 2023. Modern solutions offer:
- Biometric authentication
- Hardware tokens (FIDO2/WebAuthn)
- Mobile app-generated time-based codes
- Secure SMS and push notifications

Single Sign-On (SSO)
SSO centralizes identity management while improving user experience and security. Integration with recognized identity providers (Azure AD, Okta, Google Workspace) ensures high security standards and simplified administration.
Zero Trust Architecture
The Zero Trust model assumes no implicit trust, requiring verification for every access request. This approach is particularly effective against insider threats and compromised credentials.
Surveillance and intrusion detection
Next-generation detection systems
Modern IDS/IPS systems use artificial intelligence to analyze user behavior and detect anomalies. Behavioral analytics identifies suspicious activities based on normal usage patterns, while threat intelligence integration provides real-time awareness of known attack vectors.
Real-Time monitoring
24/7 surveillance becomes standard with automated alerts for:
- Suspicious login attempts
- Unauthorized file modifications
- Abnormal traffic spikes
- Atypical user behaviors
Security operations centers (SOC)
Managed security services provide expert monitoring and response capabilities, especially valuable for organizations lacking internal security expertise.
Backup and disaster recovery
The 3-2-1 Strategy
The 3-2-1 rule remains the reference: 3 copies of data, on 2 different media, with 1 copy off-site. Modern implementations include:
- Incremental backups to optimize storage and time
- Encryption of backups to protect sensitive data
- Automated restoration testing to validate integrity
- Geo-distributed storage for disaster resilience
Recovery objectives
Organizations now target Recovery Time Objectives (RTO) under 4 hours for critical systems, requiring high-availability architectures and automated failover systems.
Secure hosting and infrastructure
Choosing your hosting provider
The hosting provider forms your security foundation. Essential criteria include:
Security Certifications: SOC 2 Type II, ISO 27001, ISO 27017 for cloud servicesRedundant Infrastructure: Multiple data centers with automatic failoverIntegrated DDoS Protection: Multi-terabyte mitigation capacity24/7 Security Monitoring: Dedicated security teams
Secure cloud solutions
Platforms like AWS Shield provide automatic DDoS protection, while solutions like Webflow offer integrated security through:
- Static file generation reducing attack surface
- AWS infrastructure hosting with Cloudflare protection
- Automatic SSL certificates with transparent renewal
- Complete isolation between development and production environments
Protection Against Emerging Threats
AI-Powered Malicious Activity
Cybercriminals exploit AI to create personalized phishing campaigns and convincing deepfakes. Defense requires AI-powered solutions capable of detecting artificially generated content and analyzing behavioral patterns for anomaly detection.
Supply Chain Attacks
Attacks targeting third-party suppliers are surging. Organizations must rigorously assess partner security, impose contractual security standards, and monitor privileged access. The SolarWinds and Kaseya incidents demonstrate the devastating potential of these attacks.
Ransomware as a Service (RaaS)
The RaaS model democratizes ransomware attacks. Protection requires a Zero Trust approach with network segmentation, air-gapped backups, and robust business continuity plans. The average ransomware attack costs organizations $1.1 million.
Frequently Asked Questions About Web Security
What's the difference between HTTP/2 and HTTP/3 in terms of security?
HTTP/3 natively integrates TLS 1.3 encryption into the transport layer via QUIC, making all connections mandatory secure. HTTP/2 adds encryption on top of TCP, creating additional complexity. HTTP/3 also offers better network attack resistance through its unified architecture and improved congestion control.
How much does website security actually cost in 2025?
The minimum budget for basic security ranges from $150-300/month for SMBs, including: free SSL certificate, basic DDoS protection ($20/month), MFA ($10/user), automated backups ($30/month), and basic monitoring ($100/month). Large enterprises typically invest 5-10% of their IT budget in cybersecurity.
Are static websites really more secure?
Yes, static websites dramatically reduce the attack surface. They eliminate vulnerabilities related to server-side code execution, databases, and third-party plugins. Platforms like Webflow generate static files hosted on global CDNs, offering superior security compared to traditional CMS platforms like WordPress.
How can businesses protect against deepfake attacks?
Protection against deepfakes requires multiple layers: enhanced multi-factor authentication, cryptographic identity tokens, behavioral monitoring, and team awareness training. Organizations implement voice verification codes and validation protocols for sensitive transactions.
What's the role of GDPR compliance in web security?
GDPR compliance extends beyond data protection: it mandates strict security standards, breach notifications within 72 hours, and regular impact assessments. Non-compliance results in fines up to 4% of annual revenue. It structures a comprehensive security approach and builds customer trust.
Building a Security Strategy for 2025
Proactive vs. Reactive Approach
Modern security prioritizes prevention over correction. Instead of reacting to incidents, organizations adopt Security by Design, integrating security from system conception.
This transformation relies on three pillars: automation of security processes, artificial intelligence for predictive detection, and collaboration between technical and business teams.
Priority Action Plan
Phase 1 (0-30 days): Comprehensive security audit, TLS 1.3 certificate implementation, multi-factor authentication activation, and automated backup setup.
Phase 2 (1-3 months): DDoS protection deployment, HTTP/3 migration, team training on best practices, and incident response procedure establishment.
Phase 3 (3-6 months): Continuous monitoring implementation, regular penetration testing, security performance optimization, and vendor contract review.
The cybersecurity skills gap remains a challenge, with demand outstripping supply by 15%. Organizations must balance internal capabilities with managed security services and strategic partnerships.
Advanced Security Technologies
Artificial Intelligence in Defense
AI transforms cybersecurity through automated threat hunting, predictive analytics, and adaptive response systems. Machine learning algorithms analyze network traffic patterns to identify anomalies that traditional signatures miss.
Behavioral analytics establish baselines for normal user activity, automatically flagging deviations that might indicate compromised accounts or insider threats. These systems continuously learn and adapt to evolving attack patterns.
Cloud-Native Security
Cloud-native applications require DevSecOps integration, where security testing occurs throughout the development pipeline. Container security, API protection, and serverless security become critical considerations.
Infrastructure as Code (IaC) enables consistent security configurations across environments, while policy as code ensures compliance and governance at scale.
Web security in 2025 isn't optional—it's a business necessity. Organizations investing in comprehensive security strategies don't just protect assets: they create sustainable competitive advantage based on trust and reliability.
Technological evolution offers unprecedented opportunities: HTTP/3 revolutionizes performance while enhancing security, defensive AI combats malicious AI, and cloud solutions democratize access to enterprise-grade security.
The question isn't whether your site will be attacked, but when and how well prepared you'll be. Investing in web security today guarantees your business continuity tomorrow. As cyber threats evolve at breakneck speed, proactive security measures become the foundation of digital resilience and customer trust.
Sources and Resources
Official Sources
- CISA - Cybersecurity and Infrastructure Security Agency
- NIST Cybersecurity Framework
- FBI Internet Crime Complaint Center (IC3)

.webp)

.jpg)
.jpg)